Modern Honey Network ArcSight content
Continuing from the previous post about installing our own Modern Honey Network... all that is needed now would be the content to make some use of the intelligence we get from it. The most simple scenario we can cover, is using the IP addresses caught on our honeypot to generate alerts when identified in other sensors of our network.
First things first, we need an Active List to store our data. This will be a Fields based Active List with the following fields:
Malicious IP, Type is Address and The sub-type is IP Address
Comments, String
Our active list should be set with a TTL of a week or so (up to you again) to allow it to be efficient and not keep an IP flagged dirty for ever. The comment section as you will see below will be populated with the sensor that triggered it in the honeypot (Dionaea, Conpot, Snort or whatever).
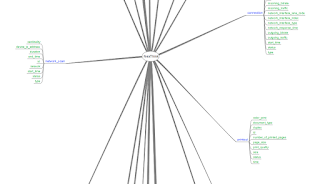
The Alerting rule needs to follow the following conditions:
event1:
( Type != Correlation AND Device Product != MHN AND InActiveList("IP-Address-WatchList"))
Actions could be up to you but for simplicity sake
On First Event:
Set Event Field Actions
name = Detected communication to IP address on WatchList
priority = 7
The Processing rule on the other hand would look something like this:
event1:
( Type != Correlation AND Device Product = MHN AND Not InActiveList("IP-Address-WatchList"))
Actions would have to be:
On First Event:
Add To Active List
Field: Attacker Address
Field: Device Custom Srting1
Resource: IP-Address-WatchList
And that's it, enjoy your fresh intel :)
First things first, we need an Active List to store our data. This will be a Fields based Active List with the following fields:
Malicious IP, Type is Address and The sub-type is IP Address
Comments, String
Our active list should be set with a TTL of a week or so (up to you again) to allow it to be efficient and not keep an IP flagged dirty for ever. The comment section as you will see below will be populated with the sensor that triggered it in the honeypot (Dionaea, Conpot, Snort or whatever).
The Alerting rule needs to follow the following conditions:
event1:
( Type != Correlation AND Device Product != MHN AND InActiveList("IP-Address-WatchList"))
Actions could be up to you but for simplicity sake
On First Event:
Set Event Field Actions
name = Detected communication to IP address on WatchList
priority = 7
The Processing rule on the other hand would look something like this:
event1:
( Type != Correlation AND Device Product = MHN AND Not InActiveList("IP-Address-WatchList"))
Actions would have to be:
On First Event:
Add To Active List
Field: Attacker Address
Field: Device Custom Srting1
Resource: IP-Address-WatchList
And that's it, enjoy your fresh intel :)